With rapid technological advances and escalating cyber threats, the need for foundations of secure digital transformation has never been more critical. At Pipeline, we understand that transforming digitally is not just about adopting new technologies but ensuring these technologies advance our cybersecurity measures. This holistic approach safeguards our operations and client data from emerging cyber threats.
The journey to secure digital transformation is pivotal for operational efficiency and building trust with clients and stakeholders. By prioritizing security in our digital transformation efforts, you can aim to enhance our capabilities and fortify your defenses against the sophisticated cyber threats of today and tomorrow.
This article explores the foundation of secure digital transformation, delves into its necessity in today's digital landscape, and underscores why cybersecurity must be at the foundation of a robust digital transformation strategy.
What is Secure Digital Transformation
Secure digital transformation is defined as integrating digital technology into all business areas, fundamentally changing how you operate and deliver value to customers. It is also a cultural change that requires organizations to continually challenge the status quo, experiment, and get comfortable with failure. However, in the cybersecurity context, it focuses explicitly on ensuring these digital transformations are secure by design.
At the recent Munich Security Conference, international security leaders emphasized the pivotal role of technology in discussions, highlighting the growing imperative for governments to invest in digitalizing their defense sectors, especially for a secure digital transformation.
Here are the basics to help you understand what is secure digital transformation:
- Holistic Approach: Secure digital transformation involves a comprehensive strategy involving technology, processes, and people.
- Advanced Technologies: Utilizing cutting-edge cybersecurity technologies such as AI and blockchain to enhance security measures.
- Risk Management: Identifying, analyzing, and mitigating digital processes and technology risks.
- Compliance and Regulations: Adhering to relevant cybersecurity laws, cloud data security, regulations, and standards to ensure compliance and protect data.
Secure digital transformation is not a one-time project but a continuous evolution of adopting secure practices and technologies. It is about creating a resilient environment where security enhancements and innovations keep pace with or outpace threats and vulnerabilities.
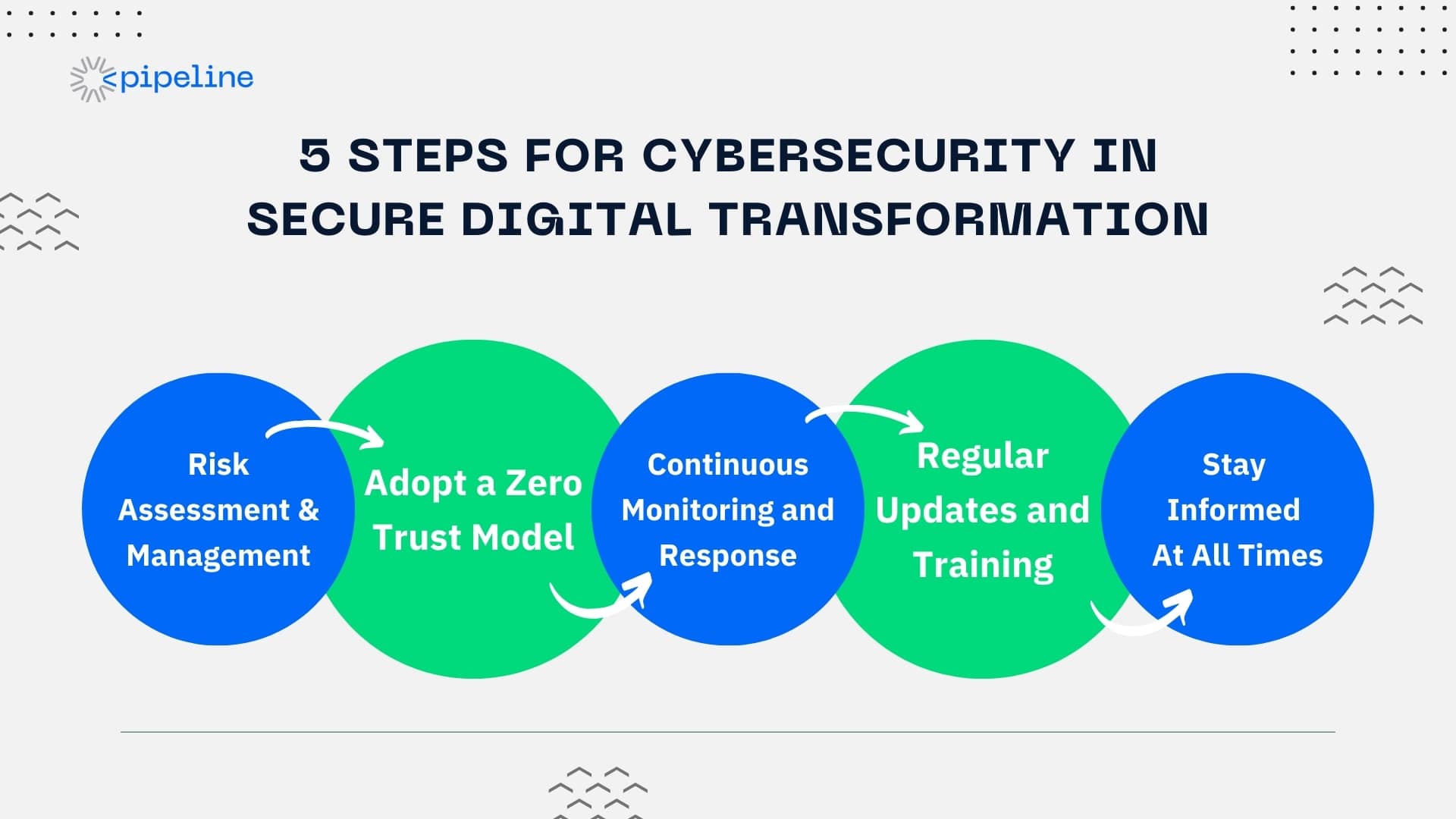
5 Steps for Cybersecurity in Secure Digital Transformation
Implementing effective cybersecurity in a digital transformation involves structured steps that ensure comprehensive security and operational continuity. Here are five essential steps to implement for cybersecurity when it comes to secure digital transformation:
- Risk Assessment and Management
Start by identifying and assessing the cybersecurity risks associated with digital transformation. Vulnerability assessment will guide the development of a targeted risk management strategy.
- Adopting a Zero Trust Model
Implement a Zero Trust security model that assumes no actors or systems should be automatically trusted, both inside and outside the organization.
- Continuous Monitoring and Response
Establish systems for continuous monitoring of your network and digital operations. This ensures timely detection and response to potential security threats.
- Regular Updates and Training
Cybersecurity is an ongoing process. Update your systems, policies, and protocols regularly. Conduct frequent training sessions to keep your team informed and vigilant.
- Stay Updated
As a management official, you are responsible for ensuring the security of your business. To help you through this rigorous process, we have prepared a list of the essential cybersecurity strategies for top management officials.
This comprehensive approach to cybersecurity is essential for maintaining the integrity and confidentiality of business operations and data in a digitally transformed environment.
Why We Need a Digital Transformation for Cybersecurity
The digital landscape and cybersecurity threats accompanying it are constantly evolving. By following these steps to digital transformation and integrating IoT strategies, businesses can ensure that their digital transformation is innovative, efficient, and secure from various cyber threats.
Digital transformation for cybersecurity is not just an option; it's necessary for survival in an increasingly digital world. Here's why:
- Cyber threats are becoming more sophisticated and pervasive. Companies need advanced cybersecurity measures to protect against these evolving threats.
- With increasing digital data, organizations must comply with stringent data protection regulations to avoid hefty fines and reputational damage.
- Integrating advanced cybersecurity measures can streamline operations and reduce the risk of costly disruptions caused by cyber incidents.
- Businesses that ensure secure digital transformations build trust with customers and stakeholders, providing a competitive edge in the market.
Different industries are now embracing secure digital transformation. Digital transformation is drastically reshaping the banking sector, introducing advanced security and privacy measures to protect customer data while enhancing service delivery through cloud technologies, as noted by MIT Technology Review.
Embracing digital transformation for cybersecurity means being proactive rather than reactive. It involves setting up robust cybersecurity frameworks, investing in cutting-edge technology, and fostering a culture of security awareness throughout the organization.
How To Prepare for Digital Transformation In Your Business
Preparing for digital transformation in any business involves more than just a technical overhaul; it requires a strategic foundation encompassing your entire organizational ethos. Here are key strategies to effectively prepare for digital transformation:
- Comprehensive Strategy Development: Begin with a robust strategy outlining the digital transformation's objectives, scope, and timeline. This should include identifying the key technologies that will drive your transformation and how these align with your business goals.
- Assess Current Technology and Infrastructure: Evaluate your current IT infrastructure and systems to determine what can be upgraded and what needs to be replaced. Understanding your starting point is crucial for a smooth transition.
- Data Management and Protection: Ensure your data management practices are up to standard. This includes data storage, processing, and protection measures to secure your data during and after the transition.
Another crucial step is to ensure proper employee training and engagement. Digital transformation is as much about people as it is about technology. Train your staff to handle new technologies and create a culture that embraces change and innovation.
The pandemic has shaped the way for securing digital transformation, and the road to digital transformation is challenging. However, with careful planning, clear objectives, and a dedicated team, businesses can achieve a seamless transition and reap the long-term benefits of being digitally advanced.
Role of Cybersecurity in Ensuring a Secure Digital Transformation
Cybersecurity is not merely an IT issue but a central component of any successful digital transformation strategy. Here’s how cybersecurity plays a pivotal role in secure digital transformations:
Building Trust with Stakeholders
Effective cybersecurity measures are crucial for protecting stakeholder data and building trust. Stakeholders need assurance that their information is secure, especially during a digital overhaul.
Protecting Digital Assets
As businesses transform, they increasingly rely on digital assets that must be adequately protected against external and internal threats.
Regulatory Compliance
Many industries are governed by strict data protection regulations. Secure cybersecurity practices ensure businesses comply with these regulations and avoid penalties and reputational damage.
Supporting Innovation
Secure environments are fertile grounds for innovation. Businesses can experiment and deploy new technologies without the looming threat of cyber incidents.
Secure digital transformation goes beyond simple technology upgrades; it represents a paradigm shift in how organizations operate and protect their digital assets. As we integrate more digital solutions into our processes, the complexity of our cybersecurity needs grows exponentially.
This transformation involves not only adopting cutting-edge technologies but also embracing a culture of continuous improvement and risk management that aligns with our strategic goals.
Pipeline Protects: Building a Secure Digital Transformation
At Pipeline, securing digital transformation is a core priority permeating every service delivery aspect. By integrating cutting-edge security measures into digital transformation strategies, Pipeline ensures that businesses adapt to new technologies with the highest security standards in mind. Here's how Pipeline protects your digital journey:
Offering Comprehensive Security Solutions
Pipeline offers various products and services to secure multiple facets of your IT infrastructure, from endpoint monitoring to threat detection through ThreatIDR and protective DNS services, alongside our email safeguard Fense. This broad spectrum of tools ensures that every component of your digital transformation is protected against potential cyber threats.
Experience Advanced Threat Detection and Response
Utilizing ThreatMDR and Vision, Pipeline equips businesses with the necessary tools to monitor, detect, and respond to threats. This proactive approach prevents potential breaches and minimizes the impact of security incidents.
Utilize Enhanced Data Protection
With services like DatalaiQ and partnerships with trusted data protection authorities like Spamhaus, Pipeline ensures that your data is secure and handled in compliance with global standards. These measures are crucial for maintaining the integrity and confidentiality of your business data throughout your digital transformation.
Confide in Strategic Risk Management
Through its security assessment and VAPT services, Pipeline helps businesses identify vulnerabilities and implement mitigation strategies. This strategic approach to cybersecurity is vital for any organization looking to transform digitally, ensuring that security considerations are integrated at every process step.
Be Informed About Compliance
Pipeline is committed to helping businesses understand and navigate the complex landscape of cybersecurity compliance. By offering comprehensive training, security assessments, and resources, Pipeline ensures your team is well-prepared to handle the new technologies and processes introduced during a digital transformation.

Pipeline's robust cybersecurity framework and expert services ensure that as your business evolves through digital transformation, it does so securely and efficiently by prioritizing security in every aspect of digital change. Contact us now for the assurance and support businesses need to innovate confidently and responsibly.